top of page


Search
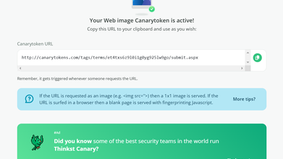
Canary tokens: threat hunting with digital trip wires
Canary tokens are digital "tripwires" that function like honeypots, designed to send a notification when triggered by a threat actor....
ghostexodusfreelan2
Mar 294 min read
0
0


A hacktivist's manifesto: The irony of Dark Storm Team’s massive DDoS attack against X
Greetings, readers. I have a question I would like to provoke your thoughts with. Whenever we think of hacktivism, what comes to mind?...
ghostexodusfreelan2
Mar 178 min read
2
0

WiFi Pineapple: a WiFi attacker’s pocket-sized superweapon
What you’re about to read is an expansion of an earlier article I wrote, ‘The powerful cyberweapons that can fit in your pocket.’ In this...
ghostexodusfreelan2
Oct 1, 20247 min read
6
0


Hackers and law enforcement: to be or not to be?
Hackers and law enforcement have a colorful history. Pick any decade, and it’s chock-full of arrests and heavy-handed prosecutions, which...
ghostexodusfreelan2
Jul 19, 20246 min read
11
0


Facebook and the fight for #opchildsafety
When the news broke on Wednesday, December 6th, that Facebook (Meta) and its offshoot Instagram were finally being served with a lawsuit...
ghostexodusfreelan2
Dec 24, 20234 min read
32
0


The psychology of internet trolls
Trolling is a form of cyberbullying. It involves posting malicious or harassing comments on social media platforms to hurt or humiliate...
ghostexodusfreelan2
Dec 24, 20235 min read
50
0


Exclusive: OSINT detectives discover crucial hints in the mystery of the teenager’s disappearance
Her name is Tatum Edwards. She was 18 years old when she vanished without a trace in 2021. She didn’t pack her bags or take any family...
ghostexodusfreelan2
Nov 20, 20239 min read
44
0


Experiment: How easy it was for me to influence Anonymous hacktivists
To say that we are living in a volatile time would be a brazen understatement. Since the onset of #OpRussia and successive operations,...
ghostexodusfreelan2
Nov 20, 20235 min read
36
1


Hackers explained: an evolution of curiosity and chaos
The first hacking incident occurred in 1878, long before computers were invented. It happened two years after the launch of Alexander...
ghostexodusfreelan2
Nov 20, 20237 min read
18
0
bottom of page

